- As of January 1, 2016, Microsoft will no longer allow certificate authorities in the Microsoft Root Certificate Program to issue certificates for SSL or code signing that use the SHA-1 hashing algorithm. SHA-2 is the preferred method now.
- Many servers are susceptible to the Heartbldeed OpenSSL Vulnerability and if yours is one of them, then you should fix that.
Benefits of using SHA-2
SHA-2 addresses some weaknesses in the SHA-1 hashing algorithm.SHA-1 is not considered to be unsafe at this time; however, the weaknesses that have been identified make the algorithm vulnerable to possible exploitation over the coming years.
Disadvantages of SHA-2
One of the drawbacks with SHA-2 is that there are some older applications and operating systems that do not support it. Compatibility problems are the main reason why SHA-2 algorithms have not been adopted more rapidly.Unsupported Technologies
- Windows XP Service Pack 2 or lower
- Apache Web Server version 1.x or lower
- Java based servers with Java SDK 1.4.1.x or lower
- Openssl version 1.0.x or lower (pre April 7, 2013)
Supported Technologies
Windows Operating Systems
- Windows Vista, 7, 8, 8.1
- Windows XP SP3
- The SHA-224 hash is not included.
Windows Servers
- Windows Server 2008, 2008 R2, 2012, 2012 R2
- Windows Server 2003 SP1 and SP2 with Hotfix KB 938397
- The SHA-224 hash is not included.
Apache
- Apache server 2.0.63 with OpenSSL0.9.8ο+
Browsers
- Internet Explorer 7+ with Windows XP SP3+
- Safari with Mac OS X 10.5+
- Firefox 1.5+
- Netscape 7.1+
- Mozilla 1.4+
- Opera 9.0+
- Konqueror 3.5.6+
- Mozilla-based browsers since 3.8+
- OpenSSL 0.9.8ο+
- Java 1.4.2+ based products
- Chrome 26+
Trends
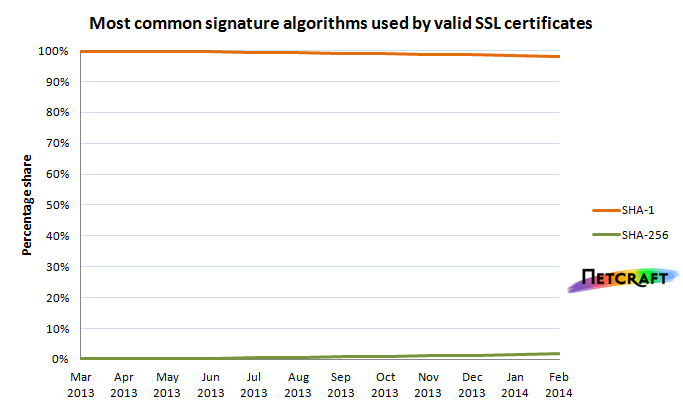
In total, more than 98% of all SSL certificates in use on the Web are still using SHA-1 signatures. Netcraft's February 2014 SSL Survey found more than 256,000 of these certificates would otherwise be valid beyond the start of 2017 and, due to the planned deprecation of SHA-1, will need to be replaced before their natural expiry dates.
SHA-256 is the most commonly used signature algorithm from the SHA-2 family, but it is used by only 1.86% of the valid certificates in Netcraft's February 2014 SSL Survey; nonetheless, this share has more than doubled in the space of 4 months, suggesting that some certificate authorities are starting to take the issue seriously. So far in 2014, more than 61% of the new certificates signed with SHA-256 were issued by a single certificate authority, Go Daddy. SHA-512 is the only other SHA-2 family algorithm to be seen used in SSL certificates, albeit deployed on only 4 websites so far.
References
http://www.entrust.net/knowledge-base/technote.cfm?tn=8526http://blogs.technet.com/b/pki/archive/2010/09/30/sha2-and-windows.aspx
http://www.zdnet.com/microsoft-pushes-crypto-standards-forward-7000023162/
http://httpd.apache.org/docs/2.2/ssl/ssl_intro.html
http://www.digicert.com/transitioning-to-sha-2.htm
https://filippo.io/Heartbleed
Excellent ! I am truly impressed that there is so much about this subject that has been revealed and you did it so nicely.
ReplyDeletewebsite development company sydney | social media marketing service